011vm
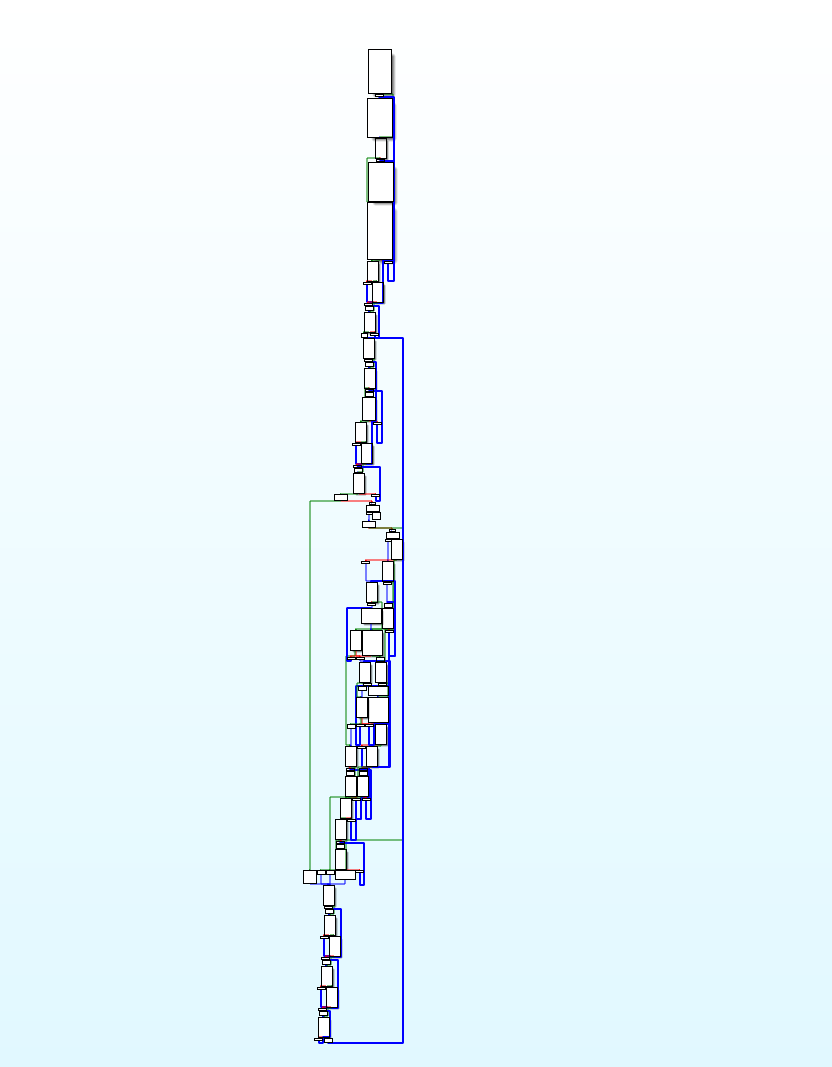
步入 main 函数,发现函数流程图长这样
反编译以后
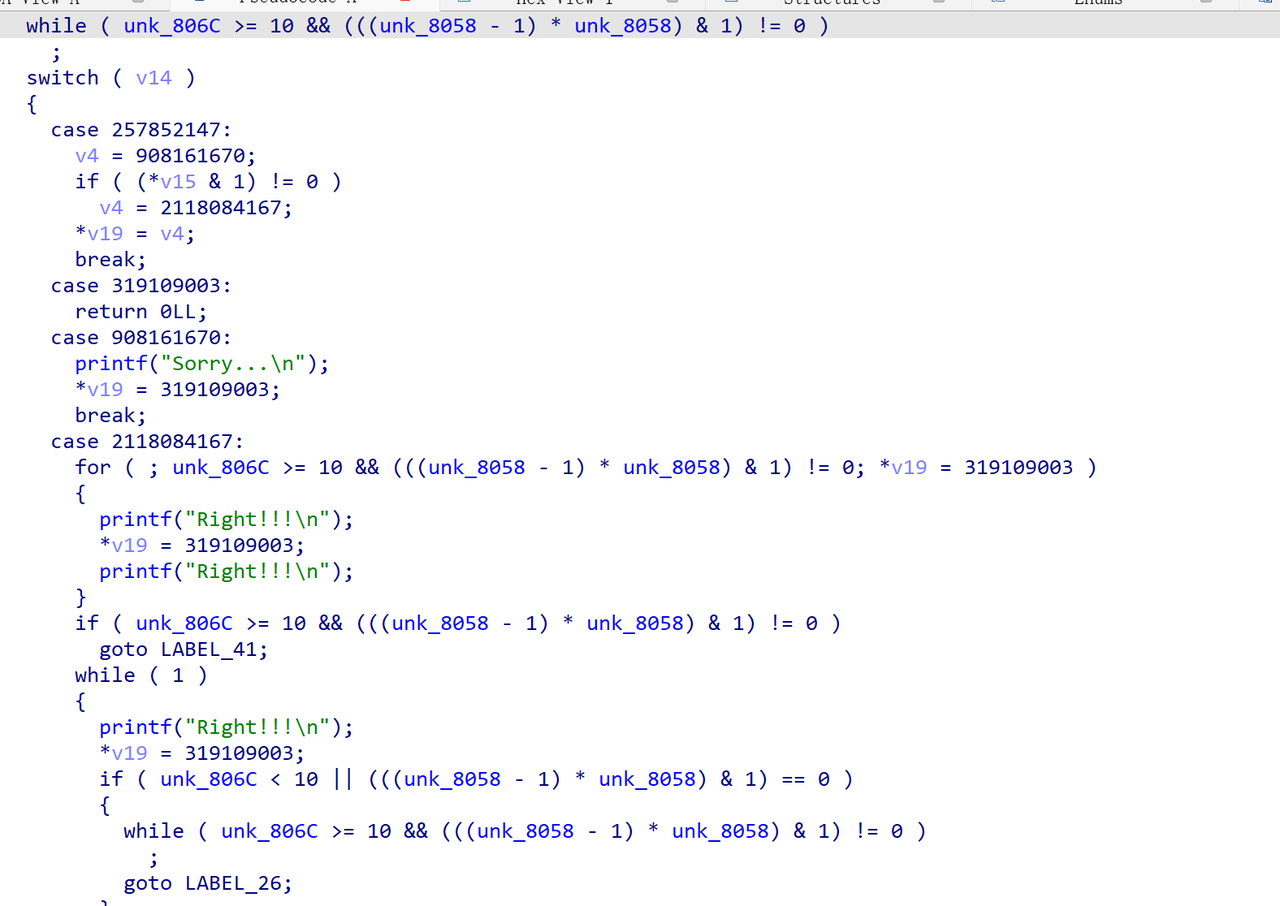
发现有控制流平坦化特征,用 d810 去控制流平坦化
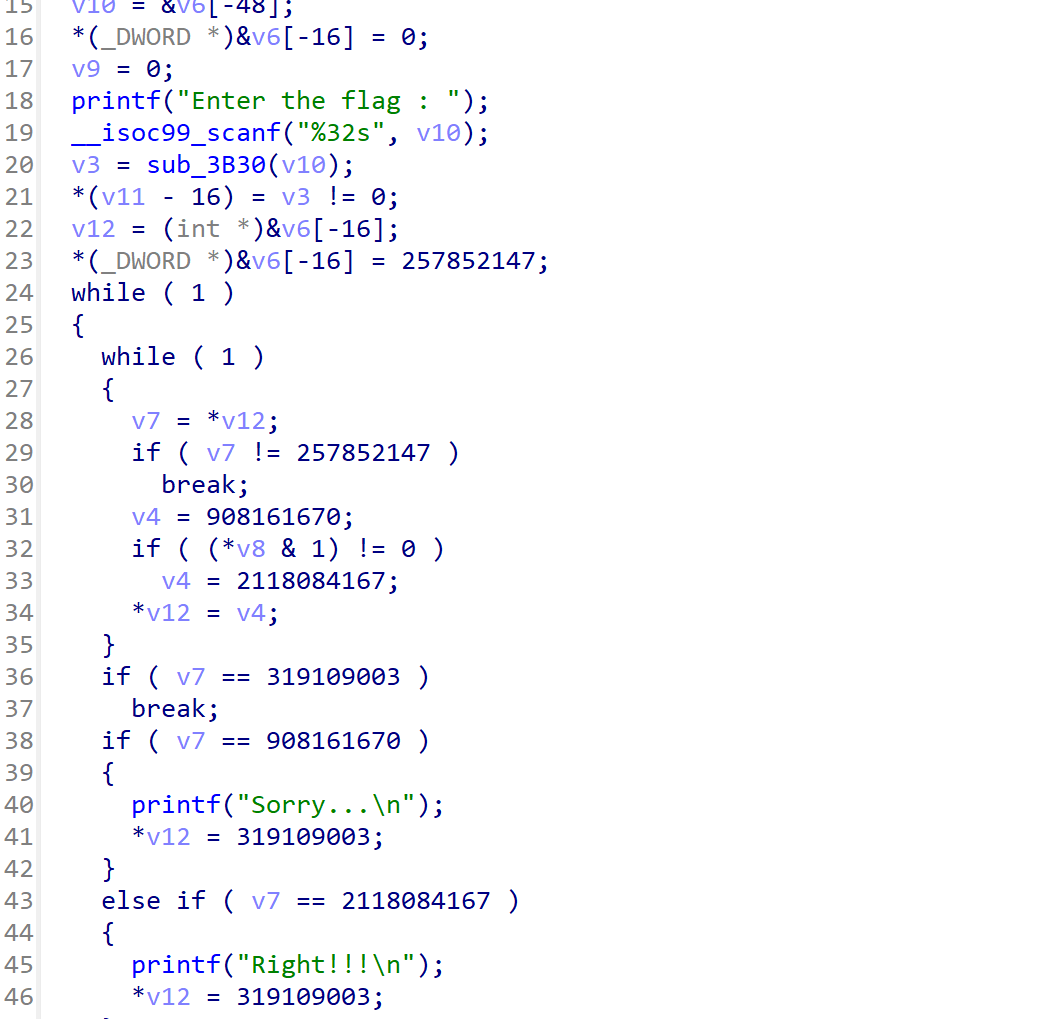
变正常多了,进入函数,发现可疑数组
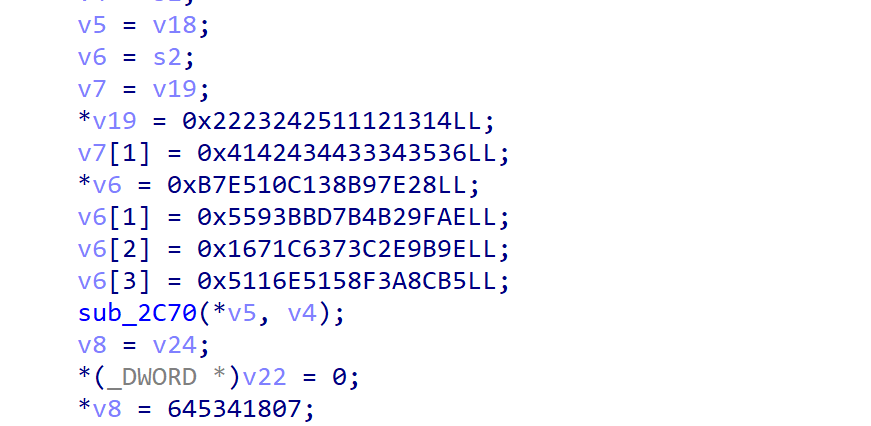
可以用 IDA 插件,IDA 8.3 自带一个插件 findcrypt(或者一个个函数搜查)
直接发现有 tea 特征
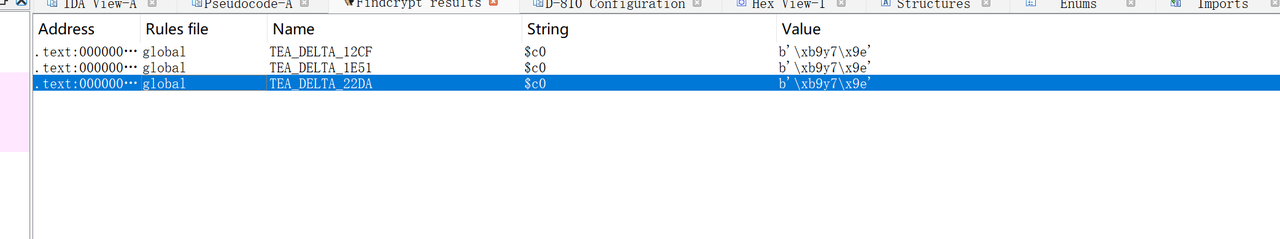

找到 tea 特征,发现未魔改,字符串也提供了,找个脚本解密得 flag
cpp
#include <iostream>
#include <string>
#include <cstdint>
using namespace std;
void TEA_decrypt(uint32_t v[2], const uint32_t key[4]) {
uint32_t v0 = v[0], v1 = v[1], sum = 0xC6EF3720, delta = 0x9e3779b9;
for (int i = 0; i < 32; i++) {
v1 -= ((v0 << 4) + key[2]) ^ (v0 + sum) ^ ((v0 >> 5) + key[3]);
v0 -= ((v1 << 4) + key[0]) ^ (v1 + sum) ^ ((v1 >> 5) + key[1]);
sum -= delta;
}
v[0] = v0;
v[1] = v1;
}
string uint32_to_string(const uint32_t decrypted[8]) {
string result;
result.reserve(32);
for (int i = 0; i < 8; ++i) {
for (int j = 0; j < 4; ++j) {
char byte = (decrypted[i] >> (8 * j)) & 0xFF; // 逐字节提取
result.push_back(byte);
}
}
return result;
}
int main() {
uint32_t key[4] = {0x11121314, 0x22232425, 0x33343536, 0x41424344};
uint32_t encrypted_flag[8] = {0x38b97e28, 0xb7e510c1, 0xb4b29fae, 0x5593bbd7,
0x3c2e9b9e, 0x1671c637, 0x8f3a8cb5, 0x5116e515};
for (int i = 0; i < 8; i += 2) {
TEA_decrypt(&encrypted_flag[i], key);
}
string decrypted_flag = uint32_to_string(encrypted_flag);
cout << "Decrypted flag: " << decrypted_flag << endl;
return 0;
}得到 flag{011vm_1s_eZ_But_C0MP1EX_!!}